November 30, 2011
November 26, 2011
November 12, 2011
October 29, 2011
October 08, 2011
September 30, 2011
August 31, 2011
August 25, 2011
August 17, 2011
July 23, 2011
June 15, 2011
June 08, 2011
June 06, 2011
Beware of twitter spam
I like many aspects of Twitter, in particular the serendipitous flow of knowledge; however I don't like the flow of spam... though it can be amusing.
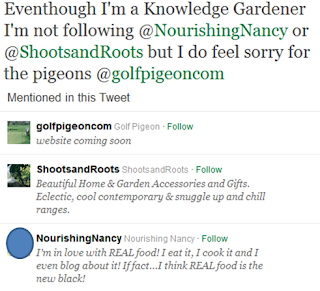
My Twitter bio title was "Knowledge Gardener" until I got fed up with followers from gardening companies and other unrelated tweeters. Below is a screenshot of a tweet in response to these followers...
I changed my bio, but still get the occasional horticultural follower, the most recent being @CultivateColo a gardening company in Colorado.
Apart from systematically blocking and reporting spam the following articles offer some additional tips:
Some useful anti spamming tools:
My Twitter bio title was "Knowledge Gardener" until I got fed up with followers from gardening companies and other unrelated tweeters. Below is a screenshot of a tweet in response to these followers...
I changed my bio, but still get the occasional horticultural follower, the most recent being @CultivateColo a gardening company in Colorado.
Apart from systematically blocking and reporting spam the following articles offer some additional tips:
Some useful anti spamming tools:
- True Twit (a validation tool)
- TwitBlock
- TwitCleaner
May 24, 2011
INF506 Evaluative Report: Part A
An evaluative statement using three experiences documented in your online learning journal (OLJ) as evidence of meeting the learning objectives of the subject (@ 750 words).
OLJ entries selected for evaluative report:
- Privacy and safety in online social networks
- Social media policies and guidelines
- Redefining content authenticity in a connected world
----------------------------------------------------------------------------------------------------------
According to a Nielsen Company 2010 report, growth in online social networking (OSN) has increased, with Australia leading the average time spent per person on social media sites (1). New social applications and tools and improved ICT infrastructure have enabled this growth; however with a different way of communicating and interacting online comes challenges. A key challenge is not about ‘getting online’ but issues around implementation and operationalisation within a framework that embraces concepts of Web 2.0 and OSN, as well as realising organisational strategic value. The three OLJ entries indicated above have been selected because they represent complex issues. Additionally, exploration of these issues by the author demonstrate the author’s understanding of the interplay between people, culture, content, process and technology.
Privacy and safety in online social networks highlights cyber-security issues associated with privacy and safety, and reasons why many people, even though they realise the importance of privacy, continue to engage in potentially risky online behaviour.
Drawing attention to the reasons for engaging in risky behaviour and the impact of these behaviours can help improve privacy and safety awareness and limit risks. For information professionals this knowledge can be used in a personal capacity to protect personal and professional information, identity and reputation (2), and in a service capacity to develop relevant literacy programs and resources that encourage online participation while mitigating privacy and safety risks. Additionally, with more information services using OSN and social media, information professionals can advocate for privacy and security feature improvements.
Despite the positive benefits associated with OSN, there is a requirement to address the risks of privacy and safety in both practice and policy (3), which is of importance when considering the ‘public’ versus ‘private’ nature of online interactions.
The blurring of lines between personal, work or educational use of OSN and social media has meant that organisations need to provide guidance in the appropriate use of these services and tools. This need has been highlighted by the increase in cases of employees being fired for inappropriate online behavior (4), which may be inadvertent or deliberate. One could therefore assume that many organisations would have, or be in the process of developing policies/guidelines; however a 2010 study indicates that only one in seven companies have formal processes associated with adopting OSN and one in five have policies concerning the use of OSN technologies (5).
While it is noted that different sectors (corporate, not-for-profit, government, education, health) will have specific issues that need addressing, the five policies/guidelines listed in a Social media policies and guidelines... a taster can be used as resources to inform the development of a social media policy or guideline.
Each resource was selected based on the ‘product’ being user-centred, jargon-free, readable and accessible (6). Additionally, these resources have not been developed in isolation; they refer to associated material including: related policies, guidelines and other documentation; training resources; communications to encourage employee engagement with and take up of the new policy/guideline; and guides for use of social media tools.
As Web 2.0, in particular OSN and social media encourages collaboration, conversation, community, content creation and co-creation, and crowdsourcing (7) policies and guidelines need to balance individuals’ right to privacy and freedom of speech with encouraging social participation and mitigating risks for individuals and the organisation (8); aspects which are highlighted in the five selected policy/guidelines.
Many policies/guidelines include good practices for online engagement. Of interest is ‘add value’ or ‘give added value to content’, which result from active user participation; a core component of Web 2.0 (9). Content generation in Web 2.0 is across multiple platforms (blogs, wikis, micro-blogs, social bookmarking, multimedia) and takes a variety of forms such as, individual thoughts, crowdsourced ideas, comments and tags. For some, ‘Web 2.0 grey content’ is considered a critical source of professional information (10), others use the insights gleaned from user-generated content (UGC) to inform their business (11), or to incorporate into learning case studies (12); while microblogging content at conferences is used as a means of co-creating knowledge (13).
This varied nature of UGC makes it hard to define and evaluate its quality and credibility. Redefining content authenticity in a connected world explores these issues. In this exploration, an area identified where information professionals can impact on the emerging field of “social construction of meaning via diverse media” (14) is by providing metaliteracy training/education, which includes traditional areas of critical thinking and information literacy as well digital, media, visual and technology literacy framed within the social constructs of emerging technologies (15).
_______________________________
Endnotes
- Led by Facebook, 2010.
- Graham, Faix & Hartman, 2009, p. 234, para. 4.
- Third, Richardson, Collins, Rahilly, & Bolzan, 2010, p. 8, para. 2.
- Grensing-Pohal, 2010, p. 1, para. 2.
- Cisco, 2010, 'The need for more governance and IT involvement in social media efforts' section, paras. 1-2.
- Junco, 2011, p. 61, para. 5.
- Hay & Wallis, 2011, 'What is Library 2.0?' section, para. 1.
- Gevertz & Greenwood, 2010.
- Levey, 2007, p. 122, para. 4.
- Bank, 2010, p. 220, para. 3.
- Ghinn, 2010.
- Kane, Robinson-Combre, & Berge, 2010, p. 64, para. 6f.
- Ross, Terras, Warick & Welsh, 2011, p.231, para. 5f.
- Ipri, 2010, p. 567, para. 1.
- Mackey & Trudi, 2011.
References
Bank, M. (2010). Blog posts and tweets: the next frontier for grey literature. In D. Farace & J. Schöpfel (Eds.) Grey literature in library and information studies, pp. 227-238. [Adobe Digital Electronic versions]. doi: 10.1515/9783598441493. Available from: http://www.alia.eblib.com.au
Cisco. (2010, January 13). Global study reveals proliferation of consumer-based social networking enterprise and a growing need for governance and IT involvement [Press release]. News@Cisco. Retrieved 2011, May 20 from Cisco website: http://newsroom.cisco.com/dlls/2010/prod_011310.html
Gevertz, D. & Greenwood, G. (2010). Crafting an effective social media policy for healthcare employees. Health Lawyer, 22(6), 28-33. Retrieved from EBSCOhost.
Ghinn, D. (2010, January 5). Pharmaceutical industry: a discovery-led approach to social media. FUMSI. Retrieved from FUMSI website: http://web.fumsi.com/go/article/use/4436
Graham, J.M., Faix, A., & Hartman, L. (2009). Crashing the Facebook party. One library's experiences in the student's domain. Library Review, 58(3), 228-236. doi:10.1108/00242530910942072
Grensing-Pophal, L. (2010). The new social media guidelines. Information Today, 27(3), 1, 46-48. Retrieved from EBSCOhost.
Hay, L. & Wallis, J. (2011). Library 2.0 and participatory library services.
What is Library 2.0? [INF506, Module 3.1]. Retrieved May 20, 2011 from Charles Sturt University Website: http://interact.csu.edu.au/portal/tool/26d2b18e-4584-45cd-0045-a63fefd27c80
Ipri, T. (2010). Introducing transliteracy. What does it mean to academic libraries? College & Research Libraries News, 71(10), 532-533, 567. Retrieved from http://crln.acrl.org/content/71/10/532.full
Junco, R. (2011). The need for student social media policy. Educause Review, January/February, 60-61. Retrieved from Educause website: http://net.educause.edu/ir/library/pdf/ERM1118.pdf
Kane, K., Robinson-Combre, & Berge, Z. L. (2010). Tapping into social networking: Collaborating enhances both knowledge management and e-learning. Vine, 40(1), 62-70. doi:10.1108/03055721011024928
Led by Facebook, Twitter, global time spent on social media sites up 82% year over year. (2010, January 22). Nielsenwire. Retrieved May 20, 2011from: http://blog.nielsen.com/nielsenwire/global/led-by-facebook-twitter-global-time-spent-on-social-media-sites-up-82-year-over-year
Levy, M. (2007). Web 2.0 implications on knowledge management. Journal of Knowledge Management, 13(1), 120-134. doi:10.1108/13673270910931215.
Mackey, T.P. & Jacobson, T.E. (2011). Reframing information literacy as metaliteracy. College & Research Libraries.72(1), 62-78. Retrieved from http://crl.acrl.org/content/72/1/62.full.pdf+html
Ross, C., Terras, M., Warwick, C., & Welsh, A. (2011). Enabled backchannel: conference Twitter use by digital humanists. Journal of Documentation, 67(2), 214-237. doi: 10.1108/00220411111109449.
Third, A., Richardson, I., Collins, P., Rahilly, K., & Bolzan, N. (2011). Intergenerational attitudes towards social networking and cybersafety. A living lab. [Research report]. Melbourne: Cooperative Research Centre for Young People, Technology and Wellbeing. Retreived from http://www.interactivemediarelease.com/download.php?f=5fouxy_FINAL_Living_Lab_Report.pdf&fc=FINAL_Living_Lab_Report.pdf
In text links were made to the following OLJ blog posts
Hayward-Wright, N. (2011, May 17). A visual framework for social media implementation. Modified 2001, May 24 [blog post]. Available from: http://knowledge-bites.blogspot.com.au/2011/05/framework-for-social-media.html
Hayward-Wright, N. (2011, May 17). Social media policies and guidelines… a taster [blog post]. Available from: http://knowledge-bites.blogspot.com.au/2011/05/social-media-policies-and-guidelines.html
Hayward-Wright, N. (2011, May 14). Privacy and safety in online social networks [blog post]. Available from: http://on-socialnetworking.blogspot.com/2011/05/privacy-and-safety-in-online-social.html
Hayward-Wright, N. (2011, May 14). Redefining content authenticity in a connected world [blog post]. Available from: http://knowledge-bites.blogspot.com.au/2011/05/redefining-content-authenticity-in.html
INF506 Evaluative Report: Part B
A reflective statement on your development as a social networker as a result of studying INF506, and the implications for your development as an information professional (@ 750 words).
----------------------------------------------------------------------------------------------------------
In reflecting on my development as a social networker I refer to the list of online social networking (OSN) technologies I used prior to IN506. While the number of OSN sites has not grown, my depth of understanding about features and limitations of these services has. For example Twitter: usage as a medium to share my thoughts, pick up new ideas and links to resources has increased; my ability to write value statements in 140 characters has improved; managing connections and security has developed; and I have implemented an aggregation tool (Yoono) which combines feeds from various OSN services. As my use of Twitter has grown so has my exploration into its role as a tool for mobilising people for crisis/disaster management (1, 2). Another example is RSS, which I thought I use extensively, however now appreciate the level of complexity that can be achieved through RSS (3) and its use as a push technology for distribution of social capital (4).
Serendipitous discoveries of useful resources has assisted in my development as a social networker and information professional. Through tweets I noticed references to paper.li which aggregates your tweeter feed into a newspaper format. As a consequence, I have created OnSocialNetworking Weekly which I also use as a topic archive. Another useful discovery occurred via INF506 Facebook group, which resulted in the use of Storify to create, on behalf of a community of practice, Gamification, a curated archive of tweets and presentation from a community event.
In exploring and selecting tools and technologies I am congnisant of the need to have a strategy (5); however prior to INF506 I had not translated this into my personal/professional online environment. I now taken time to ask myself the following questions before engaging in a network (and retrospectively): what do I hope to achieve and what are the success factors, risks, and time and resource commitment? (6). Additionally, I have reframed my social networking experience within the context of a personal learning network supported by a personal learning environment (applications and tools) which will both vary depending on context. Importantly, these strategies have helped me to (try to) achieve a “balance between learning and living” (7).
An expectation from this course was to better understand the online communication ecology. I know I have more to learn with regard to online behaviour and identity across multiple communication channels; however there are some insights I have gleaned from undertaking the INF506 project (setup and online facilitation of Yammer for a community of practice) and online interactions within INF506 Facebook group:
- New communication channels, such as OSN, supplement rather than replace existing communication channels (8).
- Initial technology adoption is usually for an explicit purpose, however continued use is driven by interpersonal connections (9).
- Greater connectedness can be achieved by creating multiple points of contact (10), such as linking with fellow students via Facebook, commenting on student blogs, and following/responding on Twitter.
- Greater connectedness can be achieved by rich, meaningful, ‘of value’ and frequent communication; behavioural aspects of interpersonal trust (11).
- Greater connectedness can be achieved through reciprocity (not only taking but also giving, no matter the size of the contribution); a key mechanism for ‘bridging social capital’ (12).
- A level of emotional intelligence (intrapersonal and interpersonal skill) is required for effective positive online communication (13).
- Lurking, with ambient presence, is a valid form of legitimate peripheral participation (14); however real personal value comes when you move from passive to active participation.
The above have guided my development as a social networker and enriched my professional knowledge, specifically in the area of facilitation of communities/networks. Additionally, the process of validating observations through literature has provided an evidence base for future practice.
In considering various course readings on ‘2.0’, I would posit that beyond the ‘movers and shakers’ (15) are librarians and information professionals, myself included, who have a ‘2.0 mindset’ to run with the ‘groundswell’ offered by social technologies (16); however we are often impeded by organisational structures, systems and culture (17). For me, spending time developing social networking skills, experimenting (and having fun) with new applications and tools (such as adding a QR code and voki to my OLJ blog), scanning the horizon for new and emerging technologies, and understanding the implications of digital trends (18) has placed me in a good position to shape an organisation’s or community’s strategic planning, influence culture and support development of structures and systems that underpin the social aspects of 2.0 (19) to mobilise knowledge.
____________________________________________
Endnotes
- Briggs, 2011.
- Huang, Chan & Hyder, 2010.
- Hayward-Wright, 2011, May 8a.
- Li & Bernoff, 2008, pp. 31-34.
- Hayward-Wright, 2011, May 17.
- Bermis-Dougherty, 2010, p. 46, para. 7.
- Utech, 2008, para. 8.
- Turner, Qvarfordt, Biehl, Golovchinsky, Back, 2010, p. 848, para. 11.
- Turner et al., p. 849, para. 7.
- Smith & Trayner, 2005, p. 1, paras. 2-3.
- Abrams, Cross, Lesser & Levin, 2003, p. 65, para 6.
- Steinfield, DiMicco, Ellison & Lampe, 2010, p. 245, paras. 4-5, 246, para. 1.
- Hansen, Grange & Prosser, 2009, p. 10, para. 5.
- MacDonald et al., 2003, p. 4, ‘The value of lurking’ section, para. 1.
- Movers and shakers such as Meredith Farkas (course reading: Building Academic Library 2.0).
- Groundswell is a term coined by Li & Bernoff, 2008.
- Bennett, 2010, p. 143, para. 2.
- Hayward-Wright, 2011, May 8b.
- Hayward-Wright, 2011, May 6, ‘Social (people) underpinnings of 2.0’ list.
References
Bennett, J. (2010). Workplace impact of social networking. Property Management, 28(3), 138-148. doi:10.1108/02637471011051282
Bermis-Dougherty, A. (2010). Professionalism and social networking. PT in Motion, 2(5), 40-47. Retrieved from EBSCOhost.
Briggs, G. (2011). The twitter revolution. The Big Issue, 357,1-14 March, 15-19.
Farkas, M. (2007, November). Building academic library 2.0 [webcast]. Keynote paper presented at Academic Library 2.0, sponsored by the Librarians Association of the University of California, Berkeley Division. Retrieved from http://webcast.berkeley.edu/event_details.php?webcastid=21207
Hansen, G., Grange, L., & Prosser, C. (2010). An investigation of emotional intelligence and the use of online social media tools in organisations [White paper]. Retrieved from Knowledge Solutions website: http://www.knowledge-solutions.com.au/attachments/147_EISM_Report.pdf
Hayward-Wright, N. (2011, May 6). Librarian 2.0, or librarian in a web 2.0 environment? [blog post]. Retrieved from http://knowledge-bites.blogspot.com.au/2011/04/librarian-20-or-librarian-in-web-20.html
Hayward-Wright, N. (2011, May 8a). The simplicity and power of RSS [blog post]. Retrieved from http://knowledge-bites.blogspot.com.au/2011/05/simplicity-and-power-of-rss.html
Hayward-Wright, N. (2011, May 8b). Digital trends and digital behaviour [blog post]. Retrieved from
http://knowledge-bites.blogspot.com.au/2011/05/did-you-know-4.html
Hayward-Wright, N. (2011, May 17). A visual framework for social media implementation. [blog post]. Modified 2011, May 24. Retrieved from http://knowledge-bites.blogspot.com.au/2011/05/framework-for-social-media.html
Huang, C., Chan, E. & Hyder, A.A. (2010). Web 2.0 and internet social networking: A new tool for disaster management? – Lessons from Taiwan. BMC Medical Informatics and Decision Making, 10(57), doi:10.1186/147269471057
Li, C. & Bernoff, J. (2008). Groundswell. Winning in a world transformed by social technologies. Boston, Mass: Harvard Business.
MacDonald, J., Atkin, W., Daugherity, F., Fox, H., MacGillivray, A., Reeves-Lipscomb, D., & Uthailertaroon, P. (2003). Let’s get more positive about the term ‘lurker’. CPsquare Foundations of Communities of Practice Workshop. Retrieved from CPsquare website: http://cpsquare.org/2003/08/lets-get-more-positive-about-the-term-lurker
Smith, J.D. & Trayner, B. (2005). Weaving together online and face-to-face learning: A design from a communities of practice perspective. In G. Richards (Ed.), Proceedings of World Conference on E-Learning in Corporate, Government, Healthcare, and Higher Education 2005, 1113-1118. Chesapeake, VA: AACE. Retrieved from http://www.editlib.org/p/21337
Steinfield, C., DiMicco, J.M., Ellison, N.B. & Lampe, C. (2009). Bowling online: Social networking and social capital within the organization. Proceedings of the Fourth
International Conference on Communities and Technologies, 245-254. doi:10.1145/1556460.1556496
Turner, T., Qvarfordt, P., Biehl, J.T., Golovchinsky, G., & Back, M. (2010). Exploring the workplace communication ecology. Proceedings of the 28th International Conference on Human Factors in Computing Systems, 841-850. doi:10.1145/1753326.1753449
Utecht, J. (2008, April 3). Stages of PLN adoption [blog post]. Retrieved 2011, May 7 from: http://www.thethinkingstick.com/stages-of-pln-adoption
Related OLJ blog post
Hayward-Wright, N. (2011, March 19). Online learning journal INF506 – Assessment item 1 [blog post]. Available from: http://knowledge-bites.blogspot.com.au/2011/03/online-learning-journal-inf506.html
Social media examples created by author during course
OnSocial Networking Weekly. (changes weekly); Available from: http://paper.li/NickyHW Also available from: http://knowledge-bites.blogspot.com.au/p/onsocialnetworking-weekly.html
Gamification. (last updated 2011, May 5). Available from: http://storify.com/nickyhw/gamification
Widgets added to OLJ blog during course (subsequent to initial blog creation)
OnSocialNetworking blog QR code: http://bit.ly/mm2g2T
OnSocialNetworking blog voki: http://bit.ly/kSmVbJ
Social media tools cited in post
paper.li: http://paper.li
Storify: http://storify.com
Yoono: http://www.yoono.com
Labels:
#inf506,
change,
digital behaviour,
information,
librarian 2.0,
online behaviour,
RSS,
social media,
social networking,
strategy,
technology,
twitter,
user generated content,
web 2.0
May 15, 2011
A visual framework for social media implementation
Know your people
| source: http://forrester.typepad.com/.a/6a00d8341c50bf53ef0120a932b364970b-pi |
Segment and profile your audience
Develop different strategies for each segment
Have a strategy
 |
| source: http://forrester.typepad.com/groundswell/2007/12/the-post-method.html |
Your strategy provides a framework for conversation, discussion and critical thinking
Your strategy is about people and relationships
Technology is an enabler
Be engaged and dynamic
 |
| source: http://www.personalizemedia.com/the-future-of-social-media-entertainment-slides |
INVOLVE – live the social web, understand it, lurk, listen
CREATE – create relevant content for communities
DISCUSS – engage in two way conversation
PROMOTE – actively, respectfully, promote the content into the networks
MEASURE – monitor (audience, engagement, loyalty, influence, action)
ITERATE - iteratively develop; it's a continuous cycle
Cohesively tie your efforts together
Cohesively tie your efforts together
| Source: http://www.rossdawsonblog.com/SocialMediaStrategyFrameworkv2.pdf |
Sources
Dawson, R. (n.d.). Social media strategy framework (Beta version 2). Retrieved from http://www.rossdawsonblog.com/SocialMediaStrategyFrameworkv2.pdf
Bernoff, J. (2009, January 19). Social technographics: Conversationalists get onto the ladder [blog post]. Retrieved from http://forrester.typepad.com/groundswell/2010/01/conversationalists-get-onto-the-ladder.html
Bernoff, J. (2007, December 11). The POST Method: A systematic approach to social strategy [blog post]. Retrieved from http://forrester.typepad.com/groundswell/2007/12/the-post-method.html
Hayes, G. (2008, October 26). Future of social media entertainment [blog post]. Retrieved from http://www.personalizemedia.com/the-future-of-social-media-entertainment-slides/
Li, C. & Bernoff, J. (2008). Chapter 3. The social technographics profile In Groundswell. Winning a world transformed by social technologies. Boston, Mass.: Harvard Business Press. Excerpt available from http://www.forrester.com/groundswell/assets/groundswell_excerpt.pdf
Saddington, J. (2010, April 15). Using POST method to craft a social media strategy for ministry [blog post]. Retrieved from http://churchm.ag/using-the-post-method-to-craft-a-social-media-strategy-for-ministry
updated: 2011, May 24
May 14, 2011
Social media policies and guidelines... a taster
When developing a social media policy consulting relevant polices and guidelines is good practice to inform your knowledge. Depending on your organisation and sector, the following resources may be useful.
 Social Media Policy
Social Media Policy
Victorian Department of Justice | 24 March 2011 | Licensed under Creative Commons Attribution-ShareAlike 3.0 Unported License | web page
A good example of a well constructed policy as it includes scope, compliance, definitions, related policies, references, status and review process.
Social Media policy includes: overview/ principle, general responsibilities as a public sector employee, compliance, identifying inappropriate use, definitions (social media tools), statement of policy (professional and personal use), guidance for navigating legal issues.
Also includes an excellent 4:20 min YouTube to promote the policy and engage employees.
Social Media Guidelines
NSW Department of Education & Training | 15 March 2011 | 4 page PDF
A concise and well written policy. First page recognises importance of online conversations and the social voice, while promoting responsible engagement in social media activities. There are 12 social media rules of engagement which are listed in a one page summary. A more detailed explanation of each rule is provided over the next two pages.
This Guideline is also supported by a Social Media Policy (28 March 2011) which provides standards of use when engaging in online conversations.
For DET staff additional internal support material is available: “Online Social Media and Technology Guide for staff” and Intranet section on “Communication Planning and Management”.
Social Media Action Plan – Part 1: Policy
Victorian Department of Health | Final Version 1.0, 2010 | Creative Commons Attribution-Noncommercial-Share Alike 2.5 Australia Licence | web page and 14 page PDF
An example of a well constructed policy. The Forward, Introduction and Scope contextually frame the policy and clearly define how and when the policy applies. The next section details the Department’s Social Media Register for Departmental Web 2.0 initiative, including conduct guidelines for social media engagement. The final sections cover social media engagement for business purposes and for personal purposes. Finally roles and responsibilities are clearly identified.
The Policy forms a 3 part series in a social media action plan, which also includes Part 2: Staff toolkit (guidelines and templates for implementing social media) and Part 3: Reference guide (description and tips for usage of major social media platforms and tools)
Social Media - Telstra’s 3 Rs of Social Media Engagement
Telstra | 14 April 2009 (?) | 6 page PDF
Having stated the intent and application of the document, the focus is on the 3 R’s of Telstra’s social media engagement: representation, responsibility and respect, which are framed against social media engagement for business purposes and other uses of social media platforms. The policy also highlights consequences of breach of policy and indicates related policies.
Read what a Telstra employee says about the policy. Also see the excellent supporting Online Training Module for and read associated Telstra news release with embedded YouTube.
Social media guidelines for IFRC staff
Internal Federation of Red Crescent Societies | October 2009 | 8 page PDF
A visually well presented and constructed document, with citation of other documents used in the development of the guideline. The introduction is one page and notably includes a section which highlights “why personal and private are not the same” on the web. The next section details 12 best practices when using social media and is interspersed with examples. The last section covers existing rules and obligations and their application to social media.
Also see IFRC related blog post and another post with comments about why create a guideline and an approach to implementation.
Social Media Policies and Guidelines Meta Lists
Social Media Policies list
Compiled by Social Media Biz (update unverified)
Categories: corporations, news organisaions, nonprofits, government, hospitals and health sector, additional resources.
Policies database
Compiled and updated by Chris Boudreaux, Social Media Governance
Categories: Agencies (advertising, PR, marketing), business products or services, consumer products or services, healthcare, government or non-profit, general guidelines and templates.
Behavioural and etiquette guidelines for organisations
Compiled by Laurel Papworth, 24 April 2009
40 listed resources. Also includes useful flow charts from US Airforce on assessing blog interactions.
Web 2.0 Governance Polices and Best Practice
Compiled and updated by US Federal Web Manager’s Council.
Grouped by public and private sector, and general and specific.
Social Media Policies
Complied and updated by Health Libraries Wiki Canada
Categories: Australia, General policies (Archives, libraries and museums), Health sector and hospitals (Public sector, University resources, State resources, Private sector, Policy tools and best practice), Best Practices Toolkit and References.
Icon used in this post sourced from http://www.davaowebdesign.com
Victorian Department of Justice | 24 March 2011 | Licensed under Creative Commons Attribution-ShareAlike 3.0 Unported License | web page
A good example of a well constructed policy as it includes scope, compliance, definitions, related policies, references, status and review process.
Social Media policy includes: overview/ principle, general responsibilities as a public sector employee, compliance, identifying inappropriate use, definitions (social media tools), statement of policy (professional and personal use), guidance for navigating legal issues.
Also includes an excellent 4:20 min YouTube to promote the policy and engage employees.
NSW Department of Education & Training | 15 March 2011 | 4 page PDF
A concise and well written policy. First page recognises importance of online conversations and the social voice, while promoting responsible engagement in social media activities. There are 12 social media rules of engagement which are listed in a one page summary. A more detailed explanation of each rule is provided over the next two pages.
This Guideline is also supported by a Social Media Policy (28 March 2011) which provides standards of use when engaging in online conversations.
For DET staff additional internal support material is available: “Online Social Media and Technology Guide for staff” and Intranet section on “Communication Planning and Management”.
Victorian Department of Health | Final Version 1.0, 2010 | Creative Commons Attribution-Noncommercial-Share Alike 2.5 Australia Licence | web page and 14 page PDF
An example of a well constructed policy. The Forward, Introduction and Scope contextually frame the policy and clearly define how and when the policy applies. The next section details the Department’s Social Media Register for Departmental Web 2.0 initiative, including conduct guidelines for social media engagement. The final sections cover social media engagement for business purposes and for personal purposes. Finally roles and responsibilities are clearly identified.
The Policy forms a 3 part series in a social media action plan, which also includes Part 2: Staff toolkit (guidelines and templates for implementing social media) and Part 3: Reference guide (description and tips for usage of major social media platforms and tools)
Telstra | 14 April 2009 (?) | 6 page PDF
Having stated the intent and application of the document, the focus is on the 3 R’s of Telstra’s social media engagement: representation, responsibility and respect, which are framed against social media engagement for business purposes and other uses of social media platforms. The policy also highlights consequences of breach of policy and indicates related policies.
Read what a Telstra employee says about the policy. Also see the excellent supporting Online Training Module for and read associated Telstra news release with embedded YouTube.
Internal Federation of Red Crescent Societies | October 2009 | 8 page PDF
A visually well presented and constructed document, with citation of other documents used in the development of the guideline. The introduction is one page and notably includes a section which highlights “why personal and private are not the same” on the web. The next section details 12 best practices when using social media and is interspersed with examples. The last section covers existing rules and obligations and their application to social media.
Also see IFRC related blog post and another post with comments about why create a guideline and an approach to implementation.
Social Media Policies list
Compiled by Social Media Biz (update unverified)
Categories: corporations, news organisaions, nonprofits, government, hospitals and health sector, additional resources.
Policies database
Compiled and updated by Chris Boudreaux, Social Media Governance
Categories: Agencies (advertising, PR, marketing), business products or services, consumer products or services, healthcare, government or non-profit, general guidelines and templates.
Behavioural and etiquette guidelines for organisations
Compiled by Laurel Papworth, 24 April 2009
40 listed resources. Also includes useful flow charts from US Airforce on assessing blog interactions.
Web 2.0 Governance Polices and Best Practice
Compiled and updated by US Federal Web Manager’s Council.
Grouped by public and private sector, and general and specific.
Social Media Policies
Complied and updated by Health Libraries Wiki Canada
Categories: Australia, General policies (Archives, libraries and museums), Health sector and hospitals (Public sector, University resources, State resources, Private sector, Policy tools and best practice), Best Practices Toolkit and References.
Icon used in this post sourced from http://www.davaowebdesign.com
Redefining content authenticity in a connected world
Two main attributes are taken into consideration when evaluating the authenticity of information: quality and credibility (1). However, with the availability of vast quantities of user-generated content in multiple formats, these attributes are becoming harder to easily validate. Furthermore, as Web 2.0 encourages a participatory and collaborative environment of information generation, seeking and use, consideration needs to be given to how authenticity is depicted in relation to the traditional method of peer-review (2).
Wikipedia, created through crowdsourcing of third party resources (3), is a primary source for many information seekers (4, 5). While Wikipedia has policies and procedures relating to verifiability of sources and presentation of a neutral point of view (6), there is debate about the quality of Wikipedia content, which ranges from something comparable to an encyclopedia entry, to a veritable mishmash of ideas which can also lack citations (7). Additionally, as Wikipedia allows author anonymity, it is difficult for information seekers to verify the credibility of an entry (8, 9).
Increasingly there is a shift to break down barriers between the traditional arbitrators of quality content (academia, publishers, libraries) and the wider community (10), which in turn “calls into question standard notions of what constitutes authority, [hence authenticity], by emphasizing the benefits of knowledge sharing via social networks” (11).
User generated content from websites, wikis, blogs, micro blogs, multimedia sources (presentations, podcasts and vodcasts) and feedback elements in information sources, such as comments and tags, is being used to inform information seekers for a variety of purposes, including health decision making to educational and research purposes. For example, a personal experience added to a photograph can inform academic research (12), or tweets about scholarly issues may lead to concepts that can be incorporated into the research process (13).
However, information sources located in these participatory online sites tend to be more opinion based (14), therefore the information seeker needs to critically review this dynamic content in order to distinguish between fact and opinion “before incorporating these ideas into his or her own knowledge” (15). Additionally, information seekers must be prepared to create an information context when evaluating resources which integrates multiple formats (16); that is, the information seeker must not only evaluate an online site for credibility, but each entry within that site (17) and the content within the entry.
Two key messages:
- The traditional peer-review quality control model of authenticity needs to be reconsidered in light of the participatory culture of Web 2.0.
- Critical thinking skills and information literacy need to be combined with other literacy skills (digital, media, visual and technology) in order to encompass the varied user generated content and contexts of Web 2.0.
__________________________________
Endnotes
- O’Grady et al., 2009, para. Content.
- Wittenberg, 2007, para. 5.
- A pillar of Wikipedea is “No original thought”. http://en.wikipedia.org/wiki/Wikipedia:Verifiability#Original_research
- Garfinkel, 2009, p. 84, paras. 1-2.
- Lorenzo, 2007, p. 8, paras. 4-6.
- See Wikipedia: Verifiablity http://en.wikipedia.org/wiki/Wikipedia:Verifiability Neutral Point of View http://en.wikipedia.org/wiki/Wikipedia:Neutral_point_of_view
- Lorenzo, 2007, p. 8, paras. 8-9.
- Wittenberg, 2007, para. 7.
- CZ:Why Citizendium? Real names are better (last modified 2011, March 12). Retrieved from http://en.citizendium.org/wiki/CZ:Why_Citizendium%3F
- Mackey & Jacobson, 2011, p. 73, para. 1.
- Ipri, 2010, p. 533, para. 5.
- Ipri, 2010, p. 533, para. 7.
- Mackey & Jacobson, 2011, p. 73, para. 2.
- Mackey & Jacobson, 2011, p. 73, para. 3.
- Mackey & Jacobson, 2011, p. 74, para. 1.
- Mackey & Jacobson, 2011, p. 69, para 1, p. 70, para. 3f.
- O’Grady et al., 2009, para. Content.
References
O’Grady, L., Witterman, H., Bender, J. L., Urowitz, S., Wijer, D., & Jadad, A. R. (2009). Measuring the impact of a moving target: towards a dynamic framework for evaluating collaborative adaptive interactive technologies. Journal of Medical Internet Research, 11(2), e20. doi: 10.2196/jmir.1058
Garfinkel, S. (2008). Wikipedia and the meaning of truth. Technology Review, 111(6), 84-86. Retrieved from Ebsco MasterFILE Premier database.
Ipri, T. (2010). Introducing transliteracy. What does it mean to academic libraries? College & Research Libraries News, 71(10), 532-533, 567. Retrieved from http://crln.acrl.org/content/71/10/532.full
Lorenzo, G. (2007). Catalysts for change: Information fluency, Web 2.0, Library 2.0, and the new education culture. Clarence Center, NY: Lorenzo Associates. Retrieved from http://www.edpath.com/images/IFReport2.pdf
Mackey, T.P. & Jacobson, T.E. (2011). Reframing information literacy as metaliteracy. College & Research Libraries,72(1), 62-78. Retrieved from http://crl.acrl.org/content/72/1/62.full.pdf+html
Wittenberg, K. (2007). Credibility of content and the future of research, learning, and publishing in the digital environment. Journal of Electronic Publishing, 10(1). doi:10.3998/3336451.0010.101
Related blog post
Hayward-Wright, N. (2011, March 19) Preservation of online user generated content [blog post] Available from: http://on-socialnetworking.blogspot.com/2011/03/preservation-of-online-user-generated.html
May 13, 2011
Privacy and safety in online social networks
The literature (1,2) indicates that despite the importance people place on online privacy (3), they continue to disclose personal information that can expose them to possible risks such as: identity theft, malicious online behavior, online stalking and associated offline criminal activity, damage to reputation (4) and loss of job or insurance claims (5).
The main reasons cited include:
- Technological confidence in navigating the privacy settings (6) coupled with poor interface design (7), the complex and often undisclosed nature of flows between third party applications (8), and privacy and safety information being hard to find (9).
- When users are presented with the relevant information, such as a privacy policy, the majority do not read it (10), which can be partly due to the complexity of the privacy policy (11).
- An assumption by members that their social networking site is taking care of their privacy and safety (12).
- Lack of social cues in the online environment which assist people to assess the level of trust accorded to individuals they interact with (13).
- Lack of understanding of the extent of their online network, including the very tenuous weak ties (14).
- Inadequate understanding and ability to assess the long term consequences of publishing certain types of information (15,16).
- Lack of individual control over shared content, such as photos, tagging and comments (17,18).
- Inability to recongnise false identity (19).
An additional consideration is the nature of Web 2.0, in particular online social networks (OSNs) which encourage conversations and connections. Within this communication ecology people will trade off a certain level of privacy for a perceived benefit (20,21), including feeling part of a group and getting positive feedback (22). For others however, participation in OSNs will be limited until they know their privacy can be managed (23); privacy practices and security of technology (24).
While the literature (25) indicates that many individuals, in particular younger people, are more concerned about protecting and controlling access to personal information which can be used to cause social discomfort (social privacy), than the use of their personal information by social networking site and partner organisations for purposes such as social marketing (institutional privacy), due consideration needs to be given to both areas of privacy vulnerability to improve privacy awareness and limit privacy risks.
Even with individuals taking steps to reduce privacy risks, in particular changing default privacy settings to give a deeper and broader level of security and privacy, OSNs need to be better designed for improved security and safety. The following areas for improvement are indicated in the literature (26):
- Improved privacy control to make members aware of what is being shared with whom.
- Provision of network visualisation tools that show a member’s complete social network including proximity indicators.
- Mechanisms to encourage an individual to adopt better practice, such as displaying common privacy controls.
- Applications that scan for fake user profiles.
- Enhancement of mechanisms for managing shared content, in particular allowing a finer granularity of control.
- A site architecture that preserves privacy during information exchange with third party applications, which would also include assured anonymisation of data.
______________
Endnotes
- Williams, 2010, p. 42, para. 7.
- O’Murchu et al., 2004, section 3.5.
- “Privacy involves keeping information in its intended scope. Such a scope is defined by the size of the audience (breadth), by extent of usage allowed (depth), and duration (lifetime). When information is moved beyond its intended scope (be it accidentally or maliciously), privacy is breached. A breach can occur when information is shared with a party for whom it was not intended (disclosure). It can also happen when information is abused for a different purpose than was intended, or when information is accessed after its intended lifetime.” (Beye et al., 2010, p. 7, para. 2)
- James, 2010, p. 1.
- Williams, 2010, p. 42, para. 3.2.
- OFCOM, 2008, p. 8
- Williams, 2010. p. 43, para. 3.2.2.
- Williams, 2010, p. 43, paras. 3.3.5-3.3.7
- OFCOM, 2008, p. 9.
- O’Murchu et al., 2004, section 3.5.
- Williams, 2010, p. 44, para. 3.38.
- OFCOM, 2008, p. 8.
- Williams, 2010, p. 43, para. 3.2.1.
- Williams, 2010, p. 43, para. 3.3.1.
- OFCOM, 2008, p. 57, para. 3.
- Williams, 2010, p. 43f, para. 3.3.4.
- Raynes-Golden, section Understanding new privacy concerns, para. 3.
- Williams, 2010, p. 44, para. 3.3.10.
- O’Murchu et al., 2004, section 3.5, Fakesters.
- Raynes-Goldie, 2010, section Social costs and benefit
- Williams, 2010, p. 42, para. 3.1.
- OFCOM, 2008, p. 37, para. 5.
- Wenger, et al., 2009, p. 90, Table 6.7.
- Wenger et al., 2009, p. 106, para. 2.
- Raynes-Goldie, 2010, section Understanding new privacy concerns
- Williams, 2010, pp. 47-48
- Beye et al., 2010, para. 3.1.
References
Beye, M., Jeckmans, A., Erkin, Z., Hartel, P., Lagendijk, R., & Tang, Q. (2010). Literature overview - Privacy in online social networks. [Technical Report TR-CTIT-10-36] Centre for Telematics and Information Technology, University of Twente,Enschede. Retrieved from http://eprints.eemcs.utwente.nl/18648/
James, M. L. (2010). Cyber crime 2.0 versus the Twittering classes. [Briefing Note 2009-10]. Australian Parliamentary Library. Retrieved from http://www.aph.gov.au/Library/pubs/bn/sci/Cybercrime.pdf
O’Murchu, I., Breslin, J.G., & Decker, S. (2004). Online social and business networking communities. DERI Technical Report 2004-08-11. Retrieved from http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.99.4055&rep=rep1&type=pdf
OFCOM. (2008). Social networking: A quantitative and qualitative research report into attitudes, behaviours and use. [Research Document]. April 2, 2008. London: Office of Communication. Retrieved from OFCOM website: http://stakeholders.ofcom.org.uk/market-data-research/media-literacy/medlitpub/medlitpubrss/socialnetworking/
Raynes-Goldie, K. (2010). Aliases, creeping, and wall cleaning: Understanding privacy in the age of Facebook. First Monday, 15(1). Retrieved from http://firstmonday.org/htbin/cgiwrap/bin/ojs/index.php/fm/article/view/2775/2432
Wenger, E., White, N. & Smith, J.D. (2009). Digital habitats: stewarding technology for communities. Portland, OR: CPsquare.
Williams, J. (2010). Social networking applications in health care: threats to the privacy and security of health information. Proceedings of ACM/IEEE 32nd International Conference on Software Engineering, 39-49. doi:10.1145/1809085.1809091
Additional references
Australian Government initiative Stay Smart Online http://www.staysmartonline.gov.au/
Australian Government initiative Cybersmart http://www.cybersmart.gov.au/
Australian Mobile Telecommunications Association Cybersafety http://www.amta.org.au/pages/Cybersafety
Gate, G. (2010). Facebook privacy: a bewildering tangle of options [graphic]. The New York Times, 12 May 2010. Available from http://www.nytimes.com/interactive/2010/05/12/business/facebook-privacy.html
May 11, 2011
Information policy... or is it a guideline or standard?
I have found that the meaning and usage of the terms ‘policy’, ‘standard’ and ‘guidelines’ is variable and interchangeable; however Bryson (1) provides the following definitions which give some clarity:
The following table provides a summary of the various features that distinguish policy, standard and guideline from each other.
An information policy can also be guided by an organisation's information principles, for example Queensland Government Enterprise Architecture & Strategy Unit (QGEA) has produced Information principles, which “are a set of ambitions or values that departments should aspire to when making decisions regarding their information and its overall management” (2). Furthermore, information policy is set within an information framework which “is not only concerned with carefully defined legal rights or restrictions on the circulation and dissemination of information… [and] the provision of a legal and regulatory framework within which information can be stored and disseminated”, but takes into consideration technological changes and issues that impact on the development of an information literate society (6).
References:
- Policy: is a high level statement that guides the decision making process and course of action to be taken. Policies usually are mandatory.
- Policy statement: describes the policy and may be supplemented by additional statements covering: policy objective and scope; responsibility for implementation, review and audit; background issues and implementation strategies.
- Standard: provides rules about the choice and management of information and its supporting technologies, such as: protocols, data capture and transfer standards; metadata and taxonomy standards; data quality; standards for record keeping; and service levels. Compliance is recommended and often required in the case of legislative standards.
- Guideline: is usually practice based and address implementation and operational issues associated with policies and standards. Guidelines are an analysis and synthesis of related policies and standards. Guidelines inform the development of processes and procedures.
The following table provides a summary of the various features that distinguish policy, standard and guideline from each other.
Policy | Standard | Guideline | |
Purpose | High level statement guiding decision making process and course of action (1) | Rules about the choice and management of information and its supporting technologies (1) | Practical guide to addressing implementation and operational issues associated with policies and standards (1) Informs development of processes and procedures |
Document inclusions | Statement covering purpose, objectives, responsibility, related documents etc. (1) | Statement covering purpose, objectives, responsibility, related documents etc. (1) | Statement covering purpose, audience, scope, background, related documents. Implementation and operational practices. |
Level of compliance | Mandatory – high level of compliance required (2) | Compliance recommended or required (2, 4) Can have an associated performance measurement (1, 3) | Optional but recommended (2, 4) Flexibility in interpretation (3, 4) |
Lifespan | Relatively long life span; i.e. 5 years (3) | Variable life span due to changes environment, such as legislation (2) | Life span depend on associated policies and standards |
Example |
An information policy can also be guided by an organisation's information principles, for example Queensland Government Enterprise Architecture & Strategy Unit (QGEA) has produced Information principles, which “are a set of ambitions or values that departments should aspire to when making decisions regarding their information and its overall management” (2). Furthermore, information policy is set within an information framework which “is not only concerned with carefully defined legal rights or restrictions on the circulation and dissemination of information… [and] the provision of a legal and regulatory framework within which information can be stored and disseminated”, but takes into consideration technological changes and issues that impact on the development of an information literate society (6).
References:
- Bryson, J. (2007). Managing information services: A transformational approach. Burlington, Vt.: Ashgate. [Adobe Digital Editions], pp. 129-130.
- Creeson, C. (2005). Information security policies: Distinct from guidelines and standards. Excerpt from Chapter 2 In Information security policies made easy, Version 10 [online]. Retrieved from http://searchsecurity.techtarget.com/feature/Information-security-policies-Distinct-from-guidelines-and-standards
- Battista, R., Hodge, M.J., & Vineis, P. (1995). Medicine, practice and guidelines: The uneasy juncture of science and art. Journal of Clinical Epidemilogy, 48(7), 875-880. Retrieved from Science Direct
- Hendricks, H.J.M., Bekkering, G.E., van Ettekoven, H., Brandsma, J.W., van der Wees, P.J., & de Bie, R.A. (2000) Development and implementation of national practice guidelines: A prospect for continuous quality improvement in Physiotherapy. Physiotherapy, 86(10), 535-547. Retrieved from Science Direct.
- Enterprise Architecture and Strategy Unit. (2009). Information principles. (2009, September, v 1.0.0). Queensland Government Enterprise Architecture Principles. Queensland Government Chief Information Office. Retrieved from http://www.qgcio.qld.gov.au/SiteCollectionDocuments/Architecture%20and%20Standards/QGEA%202.0/Information%20Management/Information%20principles.pdf, p. 4, point 2
- Dearnley, J., & Feather, J. (2001). Information policy. The wired world: An introduction to the theory and practice of the information society (pp. 60-93). London: Library Association. [CSU Reserve], p. 85, para. 4
May 08, 2011
Digital trends and digital behaviour
"Did You Know?” (4.0), produced for the Economist's Third Annual Media Convergence Forum in New York City on October 20–21, 2009, focuses on the convergence of technology and how it has changed the media landscape.
Digital trends identified:
These digital trends can have an impact on how an individual behaves as a digital citizen. The following six digital activities and associated behaviours have been identified:
Digital trends identified:
- digital books
- online media (newspapers)
- online multimedia (TV, radio, videos)
- digital advertising
- user generated online content
- crowd sourcing (Wikipedia)
- online social networks
- leveraging of online social networks
- mobilising of social networks
These digital trends can have an impact on how an individual behaves as a digital citizen. The following six digital activities and associated behaviours have been identified:
- Access to vast quantities of mediated and unmediated information anytime anywhere will require digital literacy.
- Ability to quickly upload self created content and multimedia will require awareness of intellectual property and copyright.
- Ability to easily reuse and remix digital content will require awareness of intellectual property and copyright.
- Leveraging of online networks will require an awareness of privacy, disclosure and online safety.
- Technologies such as Twitter, that help to mobilise people into action will require an awareness of acceptable use and online safety.
- Personal and work digital environments converging will require an understanding of acceptable use.
The video states: "Convergence is everywhere. It is easier than ever before to reach a large audience, but harder than ever to really connect with it." Technology is only an enabler, people make the connections, therefore people need to take responsibility for the digital behaviour.
The simplicity and power of RSS
In a previous post I briefly discussed what RSS was and how simple it is to use. This post will explore how this simplicity can be harnessed for use by libraries and information agencies?
What does RSS do for the content producer and content aggregator?
From the content producers perspective RSS is considered a push technology for the dissemination of information (1). RSS alerts can range from the macro; whole of site, to the micro; discrete site elements such as changes in library opening hours or new library acquisitions (2).
Some content producers allow tailoring of RSS feeds; for example PubMed allows users to create an RSS feed of their search strategy, which is shown in the YouTube below. These tailored search feeds can then be incorporated into a relevant page on a library website.
RSS also allows content syndication or web syndication, which is a form of remixing and republishing of someone else's material onto your websites. For example, The German Central Medical Library provides on their home page, a news feed which is merged from syndicated scientific and medical web based content from across Germany (3). Another example is the creation of RSS lists for journal table of contents (4).
On step further in RSS aggregation is the remixing and mashup of data offered by Yahoo Pipes (5).
It should be noted that the use of external content to create RSS feed requires filtering, evaluation and organisation and therefore appropriate resources (skilled staff and time) are required.
These RSS services (granulation, tailoring, remixing) creates a relationship with the consumer and promotes the continued use of the information service.
What does RSS do for the content consumer
The provision of RSS feed by information services, such as those indicated below allows consumers to keep up to date on 'selective' content. The use of content aggregators, such as Google Readers, further allow users to customise different content streams (6) which can save time and reduce information overload.
RSS feed examples
Hart, L. G. (2007). Library 2.0: RSS feeds dynamic uses for Special Libraries. Retrieved from http://www.sla.org/pdfs/sla2007/hartrssfeeds.pdf
What does RSS do for the content producer and content aggregator?
From the content producers perspective RSS is considered a push technology for the dissemination of information (1). RSS alerts can range from the macro; whole of site, to the micro; discrete site elements such as changes in library opening hours or new library acquisitions (2).
Some content producers allow tailoring of RSS feeds; for example PubMed allows users to create an RSS feed of their search strategy, which is shown in the YouTube below. These tailored search feeds can then be incorporated into a relevant page on a library website.
RSS also allows content syndication or web syndication, which is a form of remixing and republishing of someone else's material onto your websites. For example, The German Central Medical Library provides on their home page, a news feed which is merged from syndicated scientific and medical web based content from across Germany (3). Another example is the creation of RSS lists for journal table of contents (4).
On step further in RSS aggregation is the remixing and mashup of data offered by Yahoo Pipes (5).
It should be noted that the use of external content to create RSS feed requires filtering, evaluation and organisation and therefore appropriate resources (skilled staff and time) are required.
These RSS services (granulation, tailoring, remixing) creates a relationship with the consumer and promotes the continued use of the information service.
What does RSS do for the content consumer
The provision of RSS feed by information services, such as those indicated below allows consumers to keep up to date on 'selective' content. The use of content aggregators, such as Google Readers, further allow users to customise different content streams (6) which can save time and reduce information overload.
RSS feed examples
- updates on library services or projects
- upcoming library events such as training programs
- new acquisitions (can be broken down by format and topic)
- featured resources
- latest resources catalogued
- library blogs
- current awareness services
- guideline updates
- library user notifications (eg: loans date due)
- table of contents service
- employment
- aggregation of external feeds
______________________________________
Endnotes
References
Endnotes
- Hart, 2007, Abstract.
- Wusterman, 2004, p. 404, para. 2.
- Obst, 2009, p. 35, para. 1.
- Napolitan, 2009. p.9, para. 1.
- Examples of library pipes are available at http://pipes.yahoo.com/pipes/search?q=library&x=0&y=0
- Constantinides, 2008, p. 233, 235.
References
Constantinides, E., & Fountain, S.J. (2008). Web 2.0: conceptual foundations and marketing issues. Journal of Direct, Data and Digital Marketing Practice 9(3), 231–244. doi:10.1057/palgrave.dddmp.4350098.
Napolitan, F. (2009). RSS feed applications to libraries: a brief note. Journal of the European Association of Health Libraries, 5(2), 8-9. Retrieved from http://www.eahil.net/journal
Obst, O. (2009). RSS – The Swiss Army knife of the Internet. Journal of the European Association of Health Libraries, 5(1), 33-35. Retrieved from http://www.eahil.net/journal
Wusterman, J. (2004). RSS. The latest feed. Library Hi Tech 22(4), 404-414. doi:10.1108/07378830410570511. Also available from http://www.ucd.ie/wusteman/lht/wusteman-rss.html
May 07, 2011
Connecting with your clients - social media applications and tools in libraries
Andy Burkard (2009) lists four reasons libraries should be on social media:
What are the social media tools and applications that enable two way conversations and client engagement?
Social Website
Open source web design programs
Use of social tools on website to encourage interaction, such as
VoiceThread
Social tagging
Commenting and discussing
Like-ometers
Integration of social applications into website, such as
Photo sharing (Flickr)
Podcasts and vodcasts (YouTube)
Use of tools that allow easy sharing of site content, such as
Bookmarking / Add this
Social Networking Site to complement main website
Facebook, MySpace and other social networking sites
Delivery of information and marketing of services
Simple and complex RSS feeds
Library related widgets (e.g. loan due date)
Mobile access to OPAC and other applications
Podcasts
Twitter
Skype, online chat, text message, Twitter used for service contact and virtual reference
Collaboration
Collaboration tools and applications for internal and cross organisation collaboration
Community engagement and building
Online book reading and sharing communities
Crowdsourcing
Exploration of 3D worlds and augmented reality
The above is not merely about putting in technology. For an organisation to embrace the fundamentals of social networking and social media (connecting, contributing, conversing, collaborating) there has to be a shift in the mindset of staff and the organisation towards the use of social tools, which includes:
References
Brown, L. (2010, December 21). Social media and library trends 2011 [blog post]. Retrieved from http://socialnetworkinglibrarian.com/2010/12/21/social-media-and-library-trends-for-2011 Also refer to trends list for 2009 and 2010.
Greene, C. (2010, October 26). Social media trends: Applications for higher education professionals [SlideShare]. Retrieved from http://www.slideshare.net/colleengreene/social-media-trends-applications-for-higher-education-professionals
Hayward-Wright. N. (2011, April 25). Website design [blog post]. Retrieved from http://on-socialnetworking.blogspot.com/2011/04/website-design.html
Johnson, L., Smith, R., Willis, H., Levine, A., and Haywood, K., (2011). The 2011 Horizon Report. Austin, Texas: The New Media Consortium. Retrieved from http://wp.nmc.org/horizon2011 Also refer to Horizon Report 2010
Rogers, C.R. (2010) Social media, libraries, and Web 2.0: How American libraries are using new tools for public relations and to attract new users - Third survey, November 2010. Columbia, SC: South Carolina State Library. Retrieved from http://www.statelibrary.sc.gov/docs/pr/201012_pr_social_media_survey.pdf
- Social media allows you to communicate in a medium that your clients use.
- Social media builds customer relationship, as social tools allow you to gainer feedback (positive and negative) and then respond appropriately.
- Social media allows you to market you services in a social way.
- Social media allows you to understand your clients better as it “allows conversations with your users, and these conversations often reveal important insights.”
What are the social media tools and applications that enable two way conversations and client engagement?
Social Website
Open source web design programs
Use of social tools on website to encourage interaction, such as
VoiceThread
Social tagging
Commenting and discussing
Like-ometers
Integration of social applications into website, such as
Photo sharing (Flickr)
Podcasts and vodcasts (YouTube)
Use of tools that allow easy sharing of site content, such as
Bookmarking / Add this
Social Networking Site to complement main website
Facebook, MySpace and other social networking sites
Delivery of information and marketing of services
Simple and complex RSS feeds
Library related widgets (e.g. loan due date)
Mobile access to OPAC and other applications
Podcasts
Skype, online chat, text message, Twitter used for service contact and virtual reference
Collaboration
Collaboration tools and applications for internal and cross organisation collaboration
Community engagement and building
Online book reading and sharing communities
Crowdsourcing
Exploration of 3D worlds and augmented reality
The above is not merely about putting in technology. For an organisation to embrace the fundamentals of social networking and social media (connecting, contributing, conversing, collaborating) there has to be a shift in the mindset of staff and the organisation towards the use of social tools, which includes:
- the development of processes so insights from conversations do not fall on deaf ears;
- an appropriate level of staffing to support social technology based services; and
- adequate training for staff in the maintenance and use of social tools and applications.
Brown, L. (2010, December 21). Social media and library trends 2011 [blog post]. Retrieved from http://socialnetworkinglibrarian.com/2010/12/21/social-media-and-library-trends-for-2011 Also refer to trends list for 2009 and 2010.
Greene, C. (2010, October 26). Social media trends: Applications for higher education professionals [SlideShare]. Retrieved from http://www.slideshare.net/colleengreene/social-media-trends-applications-for-higher-education-professionals
Hayward-Wright. N. (2011, April 25). Website design [blog post]. Retrieved from http://on-socialnetworking.blogspot.com/2011/04/website-design.html
Johnson, L., Smith, R., Willis, H., Levine, A., and Haywood, K., (2011). The 2011 Horizon Report. Austin, Texas: The New Media Consortium. Retrieved from http://wp.nmc.org/horizon2011 Also refer to Horizon Report 2010
Rogers, C.R. (2010) Social media, libraries, and Web 2.0: How American libraries are using new tools for public relations and to attract new users - Third survey, November 2010. Columbia, SC: South Carolina State Library. Retrieved from http://www.statelibrary.sc.gov/docs/pr/201012_pr_social_media_survey.pdf
Subscribe to:
Posts (Atom)